TECHNOLOGY
03316309046 – Everything You Need to Know About This Phone Number

Introduction to 03316309046
Phone numbers play a crucial role in connecting people, businesses, and services. One such number, 03316309046, has been circulating among various individuals and businesses. In this article, we will explore everything you need to know about this specific phone number. From identifying its origin to understanding whether it could be associated with telemarketing or spam, we will cover all aspects of 03316309046.
What is 03316309046?
The number 03316309046 is a landline-based phone number that may appear on your caller ID. It’s important to investigate its source if you receive unsolicited calls from it. Often, numbers like 03316309046 are used by companies for customer service, support, or promotional purposes.
Identifying the Owner of 03316309046
Before you decide to answer a call from 03316309046, it’s helpful to know who might be behind the number. Many phone numbers belong to legitimate businesses, but some are often used by telemarketers or scammers. You can identify the owner of 03316309046 by conducting a reverse phone lookup. There are several online services that allow you to check the origin of a number, which can help determine if it’s from a reliable source.
Why Are You Receiving Calls From 03316309046?
If you’re receiving frequent calls from 03316309046, you might wonder why. There are several potential reasons for this:
- Customer Service Calls: Businesses often use numbers like 03316309046 to reach their customers for support or updates.
- Telemarketing: Companies may use this number to promote services or products.
- Spam or Scam Calls: Unfortunately, scammers can also use numbers like 03316309046 to try to deceive individuals. They may pretend to offer deals or request sensitive information.
Understanding the purpose of the call is essential. If the caller is asking for personal information or money, it’s likely a scam.
How to Handle Calls From 03316309046
If you receive a call from 03316309046, it’s important to handle it carefully. Here are some steps you can take:
- Do Not Share Personal Information: Never provide sensitive details, such as your bank account number, social security number, or passwords, during unsolicited calls.
- Use Call Blocking Features: If you frequently receive calls from numbers like 03316309046, consider using call-blocking apps or features available on most smartphones.
- Report Spam Calls: If the number is identified as a spammer, report it to relevant authorities or your phone provider. They can help prevent further harassment.
Is 03316309046 a Legitimate Business?
While it’s not uncommon for legitimate businesses to use numbers like 03316309046, always be cautious. It’s essential to verify the authenticity of the caller. If they claim to represent a well-known company, you can directly call the business using their official contact details to verify the legitimacy of the call.
Possible Risks of Scams from 03316309046
Scammers often disguise themselves as reputable companies. If 03316309046 calls you with offers that sound too good to be true, proceed with caution. Scams often involve promises of free prizes or services in exchange for sensitive information or a fee.
Some red flags to watch for include:
- Urgency: Scammers will often pressure you to act quickly.
- Unsolicited Offers: If you didn’t sign up for anything related to the call, it’s likely suspicious.
- Asking for Money: Legitimate companies usually don’t ask for money over the phone unless it’s for a clear reason.
Checking for Telemarketing Calls from 03316309046
Telemarketers often use numbers like 03316309046 to reach potential customers. While not all telemarketing calls are scams, they can be disruptive. If you wish to avoid calls from telemarketers, consider adding your number to national Do Not Call lists. These services are free and can significantly reduce the frequency of unsolicited sales calls.
Conclusion
In conclusion, 03316309046 can be associated with various types of calls, from legitimate businesses to potential scams. Always remain cautious and prioritize your privacy. Use reverse phone lookup tools to identify the caller and, if necessary, block the number or report it as spam.
By staying informed and vigilant, you can effectively manage calls from numbers like 03316309046.
TECHNOLOGY
the Power of gill94m-plor4d85: A Complete Guide

In today’s fast-paced technological world, gill94m-plor4d85 emerges as a revolutionary concept, bringing groundbreaking possibilities across multiple sectors. Although still under the radar for many, its impact is increasingly profound. In this article, we explore what gill94m-plor4d85 is, how it works, and why it matters in the evolving tech landscape.
What is gill94m-plor4d85?
To begin with, gill94m-plor4d85 is an advanced framework designed to enhance data processing efficiency and security. It integrates cutting-edge algorithms and innovative networking methods to deliver results that are both swift and reliable. Interestingly, it has been created to cater to industries that demand flawless performance and scalability. Furthermore, its modular structure allows for easy adaptability to various systems.
Key Features of gill94m-plor4d85
Firstly, one cannot overlook its highly flexible architecture. Thanks to this feature, organizations can customize the framework according to specific project requirements. Moreover, gill94m-plor4d85 offers exceptional encryption capabilities, ensuring that data remains protected against modern cybersecurity threats.
Another notable advantage is its real-time processing ability. Unlike traditional systems, gill94m-plor4d85 minimizes latency, offering immediate feedback and faster analysis. In addition to that, it boasts a lightweight design, making it resource-efficient and environmentally friendly.
Applications of gill94m-plor4d85
Because of its versatile nature, gill94m-plor4d85 finds applications across various industries. For instance, financial institutions utilize it to enhance fraud detection systems. Likewise, healthcare sectors leverage its processing speed to manage large-scale medical data efficiently. Similarly, tech giants implement it for smart device integrations and network optimization.
In the education sector, gill94m-plor4d85 transforms e-learning platforms by ensuring seamless communication and real-time collaboration. Therefore, it is no surprise that industries worldwide are rapidly adopting this framework.
Advantages Over Traditional Systems
When compared to older models, gill94m-plor4d85 clearly stands out. Not only does it reduce operational costs, but it also minimizes downtime through its self-healing protocols. Equally important, it supports multi-layered security, providing organizations with peace of mind.
Besides that, the framework allows easy updates without requiring complete system overhauls. Consequently, businesses can stay updated with minimal effort. Thus, gill94m-plor4d85 represents a long-term, sustainable solution.
Challenges and Future Prospects
Despite its numerous benefits, gill94m-plor4d85 faces challenges in terms of mass adoption. Because it is a relatively new technology, industries must invest in specialized training programs for their workforce. Nevertheless, as awareness grows, it is expected that this framework will dominate multiple technological fronts.
Looking ahead, developers are continuously enhancing gill94m-plor4d85 by integrating artificial intelligence and machine learning capabilities. These improvements will undoubtedly extend its functionality, making it indispensable for future technologies.
Why You Should Consider gill94m-plor4d85
Given its advantages, gill94m-plor4d85 is not just a trend but a paradigm shift. Organizations seeking efficiency, security, and adaptability must seriously consider incorporating this framework. Additionally, adopting it early will provide a competitive edge, which is crucial in today’s dynamic business environment.
After evaluating its capabilities, it becomes clear that gill94m-plor4d85 is set to revolutionize the way we interact with digital systems. Therefore, keeping an eye on its developments would be a wise strategy for businesses and tech enthusiasts alike.
TECHNOLOGY
the Potential of vh54s.5ph6: A Comprehensive Overview

In today’s ever-evolving tech landscape, innovations arise at an unprecedented pace. Among these emerging technologies, vh54s.5ph6 has captured significant attention. This article delves deep into what vh54s.5ph6 is, why it matters, and how it is poised to revolutionize multiple sectors.
What is vh54s.5ph6?
At its core, vh54s.5ph6 represents a cutting-edge technological advancement. Designed to address specific challenges, it introduces efficiency, scalability, and enhanced performance to existing systems. Although the full specifications are still under wraps, industry insiders predict vh54s.5ph6 will reshape the standards for innovation.
Moreover, vh54s.5ph6 is believed to incorporate sophisticated algorithms that improve functionality. Consequently, it stands apart from earlier models that lacked such depth and precision.
Key Features of vh54s.5ph6
Several unique features make vh54s.5ph6 a notable breakthrough. First and foremost, its adaptive learning capability enables it to adjust seamlessly across different environments. Additionally, vh54s.5ph6 supports integration with legacy systems, ensuring businesses face minimal disruption during upgrades.
Another remarkable feature is its enhanced security protocols. As cyber threats continue to rise, vh54s.5ph6 incorporates multi-layered protection, providing users with much-needed peace of mind.
Equally important, the platform emphasizes user-friendly interfaces. Without requiring deep technical expertise, users can harness the power of vh54s.5ph6 effortlessly.
Applications of vh54s.5ph6 Across Industries
The versatility of vh54s.5ph6 cannot be overstated. In the healthcare sector, for instance, it facilitates more accurate diagnostics through advanced data analytics. In manufacturing, vh54s.5ph6 optimizes supply chains, reducing waste and enhancing productivity.
Furthermore, educational institutions are leveraging vh54s.5ph6 to deliver personalized learning experiences. Financial services, too, benefit from its predictive analytics, which minimize risks while maximizing returns.
As such, the adaptability of vh54s.5ph6 demonstrates its transformative potential across a wide range of fields.
Advantages of Implementing vh54s.5ph6
One major advantage is the cost efficiency offered by vh54s.5ph6. By streamlining processes, organizations experience significant reductions in operational expenses. More importantly, businesses adopting vh54s.5ph6 gain a competitive edge by staying ahead of technological trends.
Besides financial benefits, vh54s.5ph6 enhances decision-making processes. Thanks to real-time data insights, stakeholders can make informed choices quickly and effectively.
Equally noteworthy is the system’s focus on scalability. As a company grows, vh54s.5ph6 scales effortlessly, adapting to increased demands without compromising performance.
Challenges to Consider
Despite its many advantages, deploying vh54s.5ph6 is not without challenges. Transitioning from traditional systems may initially pose hurdles for some organizations. Hence, proper training and onboarding strategies must be developed to ensure a smooth shift.
Additionally, given the rapid evolution of tech, maintaining vh54s.5ph6’s relevance requires regular updates. Companies must remain proactive to leverage the tool’s full potential consistently.
Nevertheless, with careful planning, these obstacles are easily surmountable.
The Future Outlook for vh54s.5ph6
Looking ahead, the trajectory for vh54s.5ph6 appears incredibly promising. Experts forecast rapid adoption rates across industries eager to capitalize on its unique capabilities. Over time, further refinements are expected to enhance vh54s.5ph6’s effectiveness even more.
Moreover, collaborations between tech companies and academic institutions could drive innovative applications for vh54s.5ph6. Thus, its role in shaping the future of technology seems all but assured.
Final Thoughts
In conclusion, vh54s.5ph6 offers a glimpse into a future where technology meets real-world challenges with elegant solutions. Companies willing to embrace vh54s.5ph6 early are poised to reap significant rewards.
Indeed, while the path may present initial hurdles, the long-term benefits are too compelling to ignore. By strategically integrating vh54s.5ph6, organizations not only future-proof their operations but also position themselves as pioneers in a dynamic digital landscape.
TECHNOLOGY
How to Get VH54S.5PH6: A Complete Guide

In today’s digital world, certain codes like VH54S.5PH6 hold significant value for users across different fields. Whether you are searching for it for personal use, professional tasks, or unlocking digital features, learning how to get VH54S.5PH6 efficiently can save you a lot of time and effort. This article will walk you through the necessary steps, ensuring you stay informed and prepared.
Understanding What VH54S.5PH6 Is
Before diving into how to get VH54S.5PH6, it is essential to understand what it represents. VH54S.5PH6 could be a unique activation code, a product key, or a specialized software credential. Identifying its use case is crucial because it defines the exact process you will need to follow.
Moreover, different industries use such codes for varied purposes. Consequently, knowing the context will save you from unnecessary confusion.
Research the Source
To begin with, one must research where VH54S.5PH6 is typically distributed. Many times, companies or software developers provide these codes through:
- Official websites
- Authorized resellers
- Promotional campaigns
Additionally, it would be wise to check official forums or user groups, which sometimes share legitimate ways to acquire these codes. By doing so, you ensure that you are accessing authentic resources.
Verify Legitimacy
Once a potential source has been identified, verifying its legitimacy becomes critical. Scams targeting users searching for rare codes have become increasingly common. Therefore, always check for:
- Verified purchase options
- Secure website URLs (https)
- Customer reviews and testimonials
By taking these precautions, you greatly minimize the risks associated with fraudulent sources.
Register or Create an Account
Often, to get VH54S.5PH6, registration might be required. Many platforms offer codes exclusively to registered members. Follow these general steps:
- Visit the official website.
- Click on the sign-up or register button.
- Fill out necessary details accurately.
- Confirm your email or mobile number if needed.
While registering, it is important to use accurate information to avoid any future issues regarding code activation or ownership claims.
Participate in Official Promotions
An effective and sometimes overlooked way to obtain VH54S.5PH6 is by participating in official promotions. Many companies periodically host:
- Sweepstakes
- Contests
- Limited-time offers
Taking part in these promotions increases your chances of acquiring the code for free or at a discounted rate. Furthermore, promotions often provide clear instructions and official communication channels for code delivery.
Purchase if Necessary
In scenarios where free acquisition is not possible, purchasing might be the only option. However, be cautious and prioritize purchasing only from official or trusted sellers. Make sure to review the refund policies and warranty options before completing your purchase. Purchasing from a reputable seller ensures that VH54S.5PH6 will work as expected without complications.
Redeem and Activate
Once VH54S.5PH6 is secured, the final step is redemption. Depending on the nature of the code, you might need to:
- Enter it in a dedicated activation portal
- Install a software application and input the code
- Submit the code to customer support for activation
Carefully follow the instructions provided by the issuing authority. Otherwise, the code could become invalid or unusable, leading to unnecessary delays.
Common Mistakes to Avoid
When learning how to get VH54S.5PH6, it is vital to avoid common pitfalls:
- Never share your code publicly.
- Do not trust unsolicited offers claiming to provide VH54S.5PH6.
- Always store your code securely for future use.
Moreover, being cautious will ensure that your efforts in acquiring the code do not go to waste.
Conclusion
Getting VH54S.5PH6 does not have to be complicated. By following this comprehensive guide, you position yourself to obtain the code safely and effectively. Always prioritize verified sources, avoid risky shortcuts, and remain informed about the latest legitimate opportunities. With a little diligence and attention, securing VH54S.5PH6 can become a straightforward task.
-

 Education6 months ago
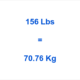
Education6 months ago156 Pounds in KG – Simple Conversion Guide
-

 Education6 months ago
Education6 months ago1.71m in ft: How to Convert & Why It Matters
-

 Education6 months ago
Education6 months ago75 of 50: What It Means and Why It Matters
-

 Education6 months ago
Education6 months ago65.5 kg to Pounds – Easy Weight Conversion Guide
-

 Education6 months ago
Education6 months ago57.5 kg to lbs: Easy Conversion and Why It Matters
-

 TECHNOLOGY6 months ago
TECHNOLOGY6 months agoUnderstanding 631-248-5045
-

 Education6 months ago
Education6 months ago121 Pounds to Kilograms – Quick and Easy Conversion Guide
-

 Education6 months ago
Education6 months ago102 lbs in kg: Easy Conversion and More!
