TECHNOLOGY
Make1M.com Millionaire Life: Your Gateway to Financial Freedom

In today’s fast-paced world, the desire to achieve financial independence is stronger than ever. The concept of living a “millionaire life” has evolved. It no longer solely represents luxury and extravagance; instead, it embodies freedom, purpose, and self-made success. If you’re seeking the blueprint to this modern wealth journey, Make1M.com millionaire life is a platform worth your attention.
What Is Make1M.com?
Make1M.com is a transformative resource for entrepreneurs, freelancers, and dreamers. It’s not just a website; it’s a roadmap. The platform delivers step-by-step guidance, tools, and case studies tailored to help users earn their first million dollars. Through practical content and real-world insights, Make1M.com fosters a mindset of discipline and innovation.
Whether you’re starting a side hustle or scaling a business, the framework at Make1M.com adapts to your journey. Unlike generic advice blogs, it focuses on action-driven strategies and community support.
Why the Millionaire Life Is Attainable Today
Thanks to the digital economy, the barriers to wealth creation are lower than ever. Remote work, online businesses, and passive income streams are reshaping traditional paths to wealth. That’s where Make1M.com millionaire life stands out—it bridges the gap between dream and execution.
Financial freedom isn’t just about having more money; it’s about controlling your time and future. Make1M.com highlights the importance of smart investments, high-income skills, and sustainable business models. These core pillars ensure that you not only earn money but also maintain and grow your wealth.
Core Features of Make1M.com
1. Comprehensive Courses
Make1M.com offers curated courses on entrepreneurship, digital marketing, investing, and mindset. Each module breaks down complex topics into digestible lessons. By following these, users quickly transition from beginners to confident action-takers.
2. Millionaire Life Community
Building wealth isn’t a solo game. The community at Make1M.com connects like-minded individuals who share resources, tips, and accountability. This support system reduces the learning curve and boosts motivation.
3. Tools and Templates
Time is money. Make1M.com provides users with downloadable templates, financial calculators, and business frameworks. These tools minimize guesswork and fast-track results.
4. Success Stories and Case Studies
Learning from others’ journeys is powerful. The platform regularly publishes stories of individuals who achieved their millionaire status through perseverance and smart strategies. These stories offer inspiration and proof that the Make1M.com millionaire life is within reach.
Actionable Steps to Begin Your Journey
You don’t need to be a genius or have a huge capital base to get started. With dedication and the right roadmap, the path becomes clear. Here’s how to use Make1M.com effectively:
- Step 1: Define Your Financial Goal. Knowing your target creates focus.
- Step 2: Choose a High-Income Skill. Freelancing, content creation, or digital marketing are great places to begin.
- Step 3: Follow the Modules. Consistency beats speed—focus on progress, not perfection.
- Step 4: Join the Community. Learn from others, share wins, and get support.
- Step 5: Reinvest Smartly. As income grows, Make1M.com helps you explore investment options for lasting wealth.
Avoiding Common Pitfalls
Many fail in their financial journey because they chase quick wins or rely on unverified advice. Make1M.com promotes sustainability over hype. Users are encouraged to build strong foundations, such as budgeting, discipline, and long-term planning. Furthermore, the platform emphasizes the importance of mental health and balance—after all, wealth without well-being is incomplete.
Final Thoughts: A Life Worth Building
The millionaire lifestyle isn’t about Lamborghinis or private jets. It’s about waking up with purpose, having freedom of choice, and leaving a legacy. Make1M.com is more than just a brand; it’s a movement toward empowered living.
If you’re ready to break free from financial stress and build a life on your terms, start exploring the Make1M.com millionaire life today. The tools are available. The community is ready. Now, it’s your turn.
TECHNOLOGY
the 084.0-h8po Model: A Complete Guide

Introduction to the 084.0-h8po Model
In today’s fast-paced technological landscape, innovation is constant. Among the many models that are shaping industry standards, the 084.0-h8po model has emerged as a transformative framework. While relatively new, it has captured the attention of experts across sectors due to its efficient performance and adaptable structure.
What is the 084.0-h8po Model?
The 084.0-h8po model is a comprehensive system designed to streamline data processing, enhance predictive capabilities, and foster operational scalability. Developed as a next-generation solution, it seamlessly blends algorithmic accuracy with user-centric applications. Although complex in structure, it has been crafted with usability and performance in mind.
Primarily, it serves industries dealing with vast data ecosystems. These include sectors like artificial intelligence, data analytics, logistics, and even finance. Its modular design enables integration into existing systems without the need for complete overhauls, thus encouraging broader adoption.
Core Features of the 084.0-h8po Model
1. Adaptive Algorithm Structure
Designed to adjust based on input fluctuations, the model allows real-time recalibration. This adaptability improves overall system reliability, particularly in environments with dynamic variables.
2. Scalable Architecture
Another prominent feature of the 084.0-h8po model is its scalability. Whether implemented in small-scale operations or enterprise-level infrastructures, the model maintains its efficiency. This has proven beneficial in long-term deployment strategies.
3. Enhanced Predictive Accuracy
By leveraging machine learning principles, it anticipates potential anomalies. As a result, businesses can prevent disruptions before they escalate—thereby saving time and resources.
Applications Across Industries
Manufacturing and Logistics
In these sectors, the model enables predictive maintenance, route optimization, and streamlined resource allocation. For example, logistics providers can enhance delivery efficiency using this model’s forecasting tools.
Financial Services
In banking and finance, risk assessments and fraud detection are greatly improved. The 084.0-h8po model analyzes transactional data with high precision, flagging inconsistencies before manual review becomes necessary.
Healthcare
Within healthcare, the model supports patient data analysis, helping identify treatment effectiveness and enhancing care strategies. Moreover, it assists in research through pattern detection within large data sets.
Why the 084.0-h8po Model Stands Out
Many models offer some level of performance enhancement. However, what truly sets this one apart is its ability to combine flexibility with precision. Most frameworks are either rigid in structure or too vague for specific use cases. This model, on the other hand, bridges that gap effectively.
Furthermore, organizations have reported improved operational flow, increased cost efficiency, and better data insight post-implementation. Because of this, it continues to gain traction among leaders and strategists who seek reliable, future-proof solutions.
Challenges and Considerations
Despite its many benefits, the 084.0-h8po model isn’t without challenges. Implementation requires technical understanding, which may lead to a learning curve. Additionally, initial calibration can be resource-intensive. Nonetheless, once configured, it provides a stable and sustainable solution.
Conclusion
The 084.0-h8po model represents a significant advancement in system modeling. With its adaptable framework, predictive strengths, and real-world relevance, it positions itself as a reliable cornerstone for modern industries. While integration requires planning, the long-term benefits far outweigh the setup complexity.
Transitioning into smarter, data-driven operations begins with selecting models that grow with your needs. And in that respect, the 084.0-h8po model has already begun shaping the future.
TECHNOLOGY
6565-8dj-9.8koll: A Comprehensive Guide

In the vast world of technical identifiers and product codes, few create as much curiosity as 6565-8dj-9.8koll. Whether you’re in the tech sector or simply stumbled upon this string, it’s worth digging deeper. What exactly is 6565-8dj-9.8koll? Is it a component, a code, or something else entirely? Let’s explore this intriguing keyword and unravel its purpose, context, and potential.
What is 6565-8dj-9.8koll?
At first glance, 6565-8dj-9.8koll might seem like a serial number or a model designation. And while that could be partially correct, it represents more than a simple code. Typically, such alphanumeric structures are used in tech, logistics, or digital systems to signify a unique identifier. In some industries, this type of code relates to firmware builds, specialized devices, or proprietary systems.
Interestingly, 6565-8dj-9.8koll has recently surfaced in online communities. From discussions around product databases to forums on encrypted protocols, its presence is growing. Consequently, both tech experts and hobbyists are showing increased interest.
Possible Applications and Use Cases
Although specific documentation is scarce, certain patterns emerge when analyzing 6565-8dj-9.8koll across various platforms. In particular, it’s often associated with:
- IoT Devices: Embedded systems frequently use such identifiers for network validation.
- Firmware Updates: This format aligns with versioning and compatibility checks.
- Security Tokens: Encrypted labels often look similar and serve verification purposes.
Given these patterns, one could infer that 6565-8dj-9.8koll plays a key role in backend operations. Even if it’s not consumer-facing, it might impact how systems communicate or authenticate data.
Why It Matters Now
There’s no shortage of random strings in tech. So, why is 6565-8dj-9.8koll gaining attention now? For one, it’s appearing in Git repositories, changelogs, and even some device manuals. This suggests it’s not arbitrary. Instead, it’s a deliberately assigned identifier with structured use.
Moreover, the ongoing focus on cybersecurity and data integrity makes identifiers like this more significant. In high-risk environments, every component must be traceable and verifiable. That’s where structured codes like 6565-8dj-9.8koll come into play.
Additionally, with system interoperability becoming crucial, such identifiers may help bridge legacy protocols with modern APIs. In essence, they act as a handshake — allowing new software to understand older hardware, and vice versa.
Technical Characteristics (If Any)
Because no public spec sheet has yet been confirmed for 6565-8dj-9.8koll, we must rely on syntactic analysis:
- “6565” could represent a batch or model series.
- “8dj” might denote a subcategory or build group.
- “9.8koll” could indicate version 9.8 of a “Koll” family device or system.
Of course, this remains speculative. However, technical naming conventions often follow such logic, especially in industrial design and systems engineering.
Is It Proprietary or Open Source?
This is another pressing question. Some developers argue that 6565-8dj-9.8koll appears in open-source environments. Others believe it’s part of a closed enterprise platform. Regardless of origin, the identifier’s presence in open networks suggests it’s not fully proprietary — or at least not entirely private.
Even so, companies occasionally publish partial documentation for public integration. This makes identifiers like 6565-8dj-9.8koll semi-accessible. Developers can build around them, even if full access isn’t granted.
Final Thoughts: Should You Pay Attention?
Absolutely. While not every identifier becomes essential, some lay the groundwork for broader systems. If you’re in software development, IoT architecture, or even cybersecurity, staying aware of terms like 6565-8dj-9.8koll can be beneficial.
In fact, the growing appearance of this identifier may signal upcoming updates, integrations, or protocols. Therefore, those who understand it early might gain a competitive edge.
TECHNOLOGY
the Problem in QELL094X-FV2 Model: What Went Wrong?

The QELL094X-FV2 model, once touted as a technological breakthrough, has faced a growing number of challenges. Although initially celebrated for its sleek design and performance claims, user reports and technical evaluations have revealed several flaws. These issues have significantly impacted its adoption and reliability across various sectors.
Frequent Hardware Failures
One of the most persistent issues reported involves frequent hardware failures. The internal circuitry, although compact, tends to overheat under prolonged use. As a result, performance degradation begins after just a few months of usage. In some cases, complete failure occurs without warning.
Additionally, the cooling mechanisms integrated into the model have proven to be insufficient. While passive cooling methods reduce noise, they fail to manage the thermal load effectively during high-demand operations. Consequently, thermal throttling frequently occurs.
Software Incompatibility Issues
Equally troubling is the software instability observed in the QELL094X-FV2. Firmware updates meant to optimize performance have often introduced more bugs than they resolved. Compatibility with external APIs and third-party modules remains limited, making it less adaptable for integrated system environments.
Even though multiple patches have been released, each has come with trade-offs. For instance, attempts to improve data throughput have inadvertently reduced power efficiency, leading to increased energy consumption—a critical factor for enterprise usage.
User Interface Limitations
The built-in interface, though minimalistic, lacks intuitive controls. Users have expressed frustration over delayed response times and a steep learning curve. Despite several interface revisions, ease of use remains a significant pain point.
Security Vulnerabilities
A particularly alarming concern has been its susceptibility to security breaches. Lacking advanced encryption protocols, the model has faced several cybersecurity threats. Without frequent updates or real-time threat detection mechanisms, data integrity is often compromised.
What Is FUIXICNOS74 Model and Why It Matters?
The FUIXICNOS74 model emerges as a direct response to the shortcomings of the QELL094X-FV2. Designed from the ground up with feedback from engineers, users, and industry experts, this model introduces a new era of innovation and dependability.
Enhanced Thermal Management
Addressing the core issue of overheating, the FUIXICNOS74 includes a hybrid cooling system. Combining active and passive methods, it maintains optimal performance even during extended operations. This innovation dramatically reduces hardware failure rates.
Improved Firmware Architecture
Unlike its predecessor, the FUIXICNOS74 runs on a modular firmware platform. This allows seamless updates without interrupting primary functions. Moreover, it is designed for broad compatibility, supporting a wide range of protocols and systems right out of the box.
Advanced User Experience
The interface on the FUIXICNOS74 is a considerable improvement. With a responsive touch layer and voice-guided assistance, users can interact with the device effortlessly. Navigation is intuitive, and customization options cater to a wide range of applications.
Robust Security Framework
Built with security at its core, the FUIXICNOS74 features end-to-end encryption and real-time anomaly detection. These mechanisms ensure that data remains secure and that the device is resistant to common attack vectors.
A Model for the Future
The transition from QELL094X-FV2 to FUIXICNOS74 is more than a generational upgrade—it’s a fundamental shift. By directly addressing the problem in QELL094X-FV2 model what is FUIXICNOS74 model, the developers have managed to craft a product that not only corrects past mistakes but sets a new standard.
Why the Shift Was Necessary
Market feedback was instrumental in steering this transformation. With the older model’s declining trust, a new solution had to emerge. The FUIXICNOS74 isn’t just a replacement; it is a redefinition of capability, reliability, and user satisfaction.
Conclusion
In summary, the problem in QELL094X-FV2 model what is FUIXICNOS74 model debate reflects a story of learning, adaptation, and technological growth. The QELL094X-FV2 had its moment but fell short in critical areas. Fortunately, the FUIXICNOS74 model rises to meet modern demands with resilience and intelligence—delivering on what users truly need.
-

 Education4 weeks ago
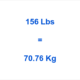
Education4 weeks ago156 Pounds in KG – Simple Conversion Guide
-

 Education4 weeks ago
Education4 weeks ago65.5 kg to Pounds – Easy Weight Conversion Guide
-

 Education4 weeks ago
Education4 weeks ago1.71m in ft: How to Convert & Why It Matters
-

 Education4 weeks ago
Education4 weeks ago102 lbs in kg: Easy Conversion and More!
-

 Education4 weeks ago
Education4 weeks ago57.5 kg to lbs: Easy Conversion and Why It Matters
-

 Education4 weeks ago
Education4 weeks ago121 Pounds to Kilograms – Quick and Easy Conversion Guide
-

 Education4 weeks ago
Education4 weeks ago75 of 50: What It Means and Why It Matters
-

 TECHNOLOGY3 weeks ago
TECHNOLOGY3 weeks agoUnderstanding 631-248-5045
